What is ransomware virus Attack?
What is ransomware? How it works and how to remove it
In 2013, modern age of ransomware began with crypto lockers. In the intervention years, aggressors have become increasingly sophisticated and business minded. Here you need to know.Ransomware is a form of malicious software (or malware), which causes harm to you after moving it to your computer, usually denies access to your data. The invader demands the ransom from the victim, promises - not always true - to restore access to data on payments.
Users have been instructed to pay the fee to get a decryption key. Costs can range from a few hundred dollars to thousands, Bitcoin is payable to cyber criminals.
How ransomware works
Many vectors can take ransomware to use the computer. One of the most common distribution systems is spam spamming - attachments that come to the victim in an email, copy as a file, they should be trusted. When they are downloaded. If they are opened, they can take the computer, especially if they have built-in social engineering tools that inspire users to allow administrative access.
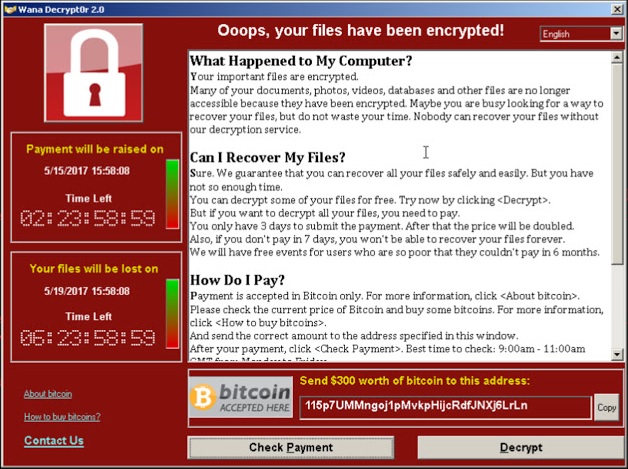
After ransomware comes in the computer, malware victim computers can do many things, but the most common action is by now to encrypt some or all user files. If you want technical details, take a deep look at the Infosacac Institute to see how many flavored files of ransomware are encrypted. But the most important thing to know is that at the end of the process, files can not be decrypted without the mathematical key known only by the attacker. A message is presented to the user stating that their files are no longer accessible and if the victim sends an undesirable bitcoin payment to the attacker then it will only be decrypted.
In some forms of malware, the attacker can claim to be a law enforcement agency to stop the victim's computer to close the computer of the victims, and may demand a payment of "fines", perhaps less likely to the victims Report to the authorities the attack. But most of the attacks are not troubled by this quarrel. There is also a difference in the name of leakware or docsware, in which the attacker threatens to propagate sensitive data on the victim's hard drive until one amount is paid. But finding and finding such information is very difficult for the attackers, the most common type of 'encryption is' nowadays.
Who is a target for ransomware?
In many different ways, they choose aggressive organizations that they target with ransomware. Sometimes this is a case of chance: For example, attackers can target universities because they have a small security team and a different user base that makes a lot of file sharing, which makes it easy to enter their security is.
How to prevent ransomware
You can take many defensive steps to prevent Ransomware infection. These steps are generally one of the best security practices, so they improve your safety after all types of attack:
To ensure that you have fewer vulnerabilities to exploit, keep your operating system patched and up-to-date.
Do not install software or give it administrative privileges until you know what it really is and what it does.
Install antivirus software that reaches malicious programs such as revenues, and detects whitelisted software, which prevents unauthorized applications from executing in the first place.
And, of course, back up your files, often and automatically! This malware attack will not stop, but the loss can be very low.
read more about automatic USB pan-drive hacking
just click on link: USB pan-drive hacking
https://www.hackerclub.tk/2018/07/how-to-make-auto-hacking-USB-drive.html



Thank you for your valuable feedback